Network Security: Fortifying Your Digital Fortress
In today's interconnected world, network security has become a paramount concern for individuals and organizations alike. With the increasing reliance on digital technologies, safeguarding sensitive information and preventing cyberattacks is essential. This comprehensive guide will delve into the fundamental aspects of network security, exploring key concepts, best practices, and emerging threats.
Introduction
In today's interconnected world, network security has become a paramount concern for individuals and organizations alike. With the increasing reliance on digital technologies, safeguarding sensitive information and preventing cyberattacks is essential. This comprehensive guide will delve into the fundamental aspects of network security, exploring key concepts, best practices, and emerging threats.
Understanding the Digital Landscape: A Network Security Primer
Network security refers to the practice of protecting computer networks and data from unauthorized access, use, disclosure, disruption, modification, or destruction. It involves a multi-layered approach to identify, assess, and mitigate potential vulnerabilities.
Network Security: Safeguarding Your Digital Assets
Introduction
In today's interconnected world, network security has become a paramount concern for individuals and organizations alike. With the increasing reliance on digital technologies, safeguarding sensitive information and preventing cyberattacks is essential. This comprehensive guide will delve into the fundamental aspects of network security, exploring key concepts, best practices, and emerging threats.
Cornerstones of Network Security: Essential Components
Network security refers to the practice of protecting computer networks and data from unauthorized access, use, disclosure, disruption, modification, or destruction. It involves a multi-layered approach to identify, assess, and mitigate potential vulnerabilities.
Shielding Your Network: Effective Security Strategies
- Firewall: A firewall acts as a security barrier, monitoring incoming and outgoing network traffic and blocking unauthorized access.
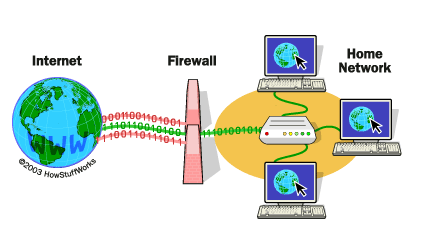
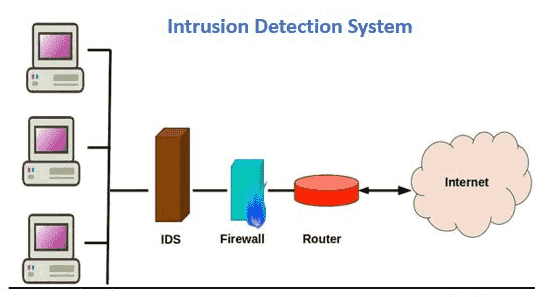
2. Intrusion Detection System (IDS): An IDS detects and alerts administrators to potential security threats, such as unauthorized access attempts or malicious activities.
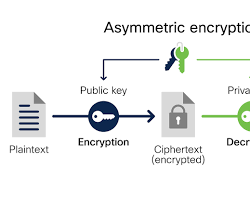
3. Encryption: Encryption converts plain text into ciphertext, making it unreadable to unauthorized individuals. It is crucial for protecting sensitive data, such as passwords and financial information.
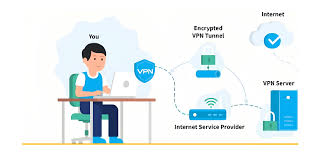
4.Virtual Private Network (VPN): A VPN creates a secure, encrypted connection over a public network, enabling remote access to private networks.
5. Access Control: Access control mechanisms regulate who can access network resources and what they can do. Strong authentication methods, such as multi-factor authentication, can enhance security.

