"Strengthening Defenses with Cybersecurity."

"Offensive cybersecurity in real-world cyberattacks to identify vulnerabilities in an organization's infrastructure. Traditional defensive strategies focused on preventing and mitigating threats, offensive cybersecurity aims to uncover potential weaknesses before malicious actors can exploit them."
What Is Offensive Cybersecurity?
Offensive cybersecurity in real-world cyberattacks to identify vulnerabilities in an organization’s infrastructure. Unlike traditional defensive strategies that focus on preventing and mitigating threats, offensive cybersecurity seeks to uncover potential weaknesses before malicious actors can exploit them. This strategy typically includes:
- Penetration Testing: Simulated attacks to discover and address system vulnerabilities.
- Red Teaming: Advanced, multi-layered attack simulations mimicking real-world threats.
- Threat Hunting: Actively searching for hidden threats within an organization’s environment.
- Vulnerability Assessments: Comprehensive evaluations of security gaps.
Key Offensive Cybersecurity Services
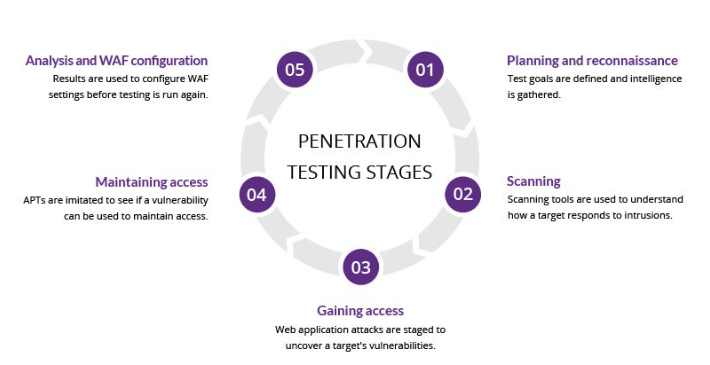
1. Penetration Testing
Penetration testing involves simulating cyberattacks on a network, application, or system to uncover vulnerabilities. These tests can be performed manually or with automated tools to mimic the tactics of real attackers.
2. Red Team Assessments
Red team assessments are full-scope simulations where a team of ethical hackers tests an organization’s defenses. Unlike penetration testing, red teaming focuses on achieving specific objectives, such as accessing sensitive data, to evaluate an organization’s detection and response capabilities.

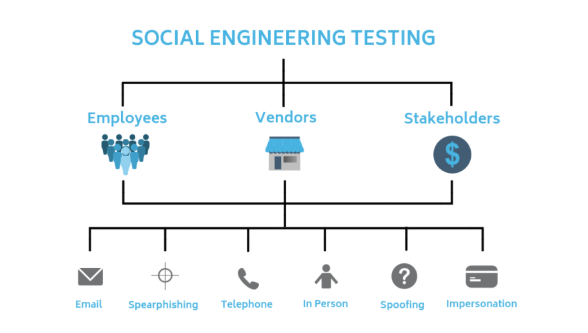
3. Social Engineering Testing
This service tests the human element of cybersecurity by simulating phishing attacks, pretexting, and other techniques to assess employee awareness and response.
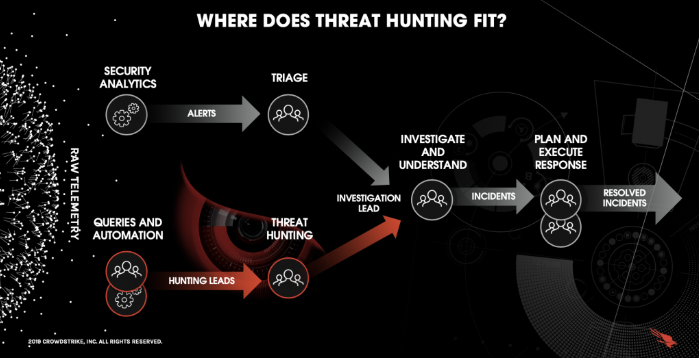
4. ADV Threat Hunting
Advance Threat hunting uses sophisticated tools and techniques to proactively search for threats that bypass traditional defenses, such as malware or insider threats.
Practices for Implementing Offensive Cybersecurity
- Partner with Experts: Work with certified cybersecurity professionals who have experience in offensive tactics.
- Conduct Regular Assessments: Cyber threats evolve rapidly, so regular testing is essential to maintain a strong defense.
- Train Your Team: Educate employees on recognizing and responding to cyber threats to strengthen the human firewall.
- Invest in Advanced Tools: Utilize state-of-the-art tools for vulnerability scanning, threat hunting, and penetration testing.
- Review and Adapt: Use insights from offensive measures to continually update and improve your cybersecurity strategies.
Final Thoughts
Offensive cybersecurity services are not just about attacking your own systems; they’re about preparing for the worst-case scenario. By identifying and addressing vulnerabilities proactively, organizations can strengthen their defenses, protect critical assets, and maintain customer trust in an increasingly hostile digital world.
Adopting a proactive approach to cybersecurity is no longer optional — it’s a necessity. If your organization is ready to take its defenses to the next level, consider implementing offensive cybersecurity measures today.
